
USING NET-SNMP UNDER LINUX AND µCLINUX
INTRODUCTION TO NETWORK MANAGEMENT

Patrice KADIONIK, Professor Assistant at the ENSEIRB School of Electrical Engineering, Telecommunication, and Computer Science
![]() French version
here
French version
here
What is Network Management? This article presents its main concepts. The SNMP
protocol which is the standard de facto in this area will have then reviewed.
The practical application of SNMP is presented by using the NET-SNMP package.
The embedded market (under Linux) is now growing exponentialy since one have added the IP connectivity on every electronic device. The traditional method for remote control of an embedded system is to use an embedded Web server. This article describes how one can make the same thing with the SNMP protocol. An electronic module connected on the PC parallel port is presented in detail and will be used for this purpose. The reader will see how to control this module by SNMP under Linux. He will also see how to make in the same way with µClinux, an embedded Linux flavour for non MMU processor.
1. Network Management
1.1. Introduction
What does the network management concept mean? The ISO organization (International Organization Standard) has defined 5 items:
In fact, one can see that a system administrator of a company, an university,
a school... has to manage also his own network. It does it without too many
problems but the difficulties grow as soon as the size of the network becomes
significant. The solution is then to rationalize, to standardize the things
and it was also proposed standards for network management.
The ISO organization has proposed in the Eighties the CMIS/CMIP standard (Common Management Information Service ISO 9595, Common Management Information Protocol ISO 9596) as protocols for network management and defines a general framework in the level structures (ISO 7498).
In parallel, the IAB society (Internet Activities Board) approves the SNMP protocol (Simple Network Management Protocol) as a short term solution and CMOT (CMIP Over TCP) as a long term solution. At the beginning of the Nineties, SNMP, simpler, becomes standard de facto and is adopted by many manufacturers. It's the standard for IP networks but for all other networks too.
1.2. SNMP Concepts
Introducton:
Allthough issued from the Internet world, the SNMP protocol (Simple Network Management Protocol) has been developed in the Eighties and is based on many ideas issued form the ISO CMIS/CMIP protocol.
SNMP is defined in the RFC 1157 (Request For Comments). It uses the concept of Client/Server application well-known in Internet world:
One thus finds 3 significant elements in SNMP:
SNMP Protocol:
SNMP is a protocol built on the top of UDP/IP:
| SNMP |
| UDP |
| IP |
| Layers 1 and 2 |
The use of the UDP protocol is justified for its simplicity,
its speed and its concision (8 byte header against 20 byte header for TCP),
which makes it possible to very quickly send alarms to a SNMP manager. Unfortunately,
it's a transport connectionless protocol and is also unreliable, which means
that SNMP messages may be lost...
5 types of SNMP messages or SNMP requests can be exchanged (SNMPv1) between a SNMP agent and a SNMP manager:
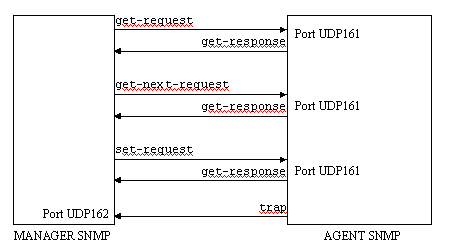
Figure 2: SNMP requests and UDP port numbers
SNMP uses UDP port 161 from the agent side for SNMP GET, GETNEXT and SET requests and UDP port 162 for SNMP TRAPs from the manager side.
The general structure a SNMPv1 get-request, get-next-request, set-request and get-response request is built as following:
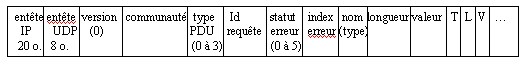
Figure 3: IP datagram for a SNMP request
The general structure of a SNMPv1 trap is built as following:
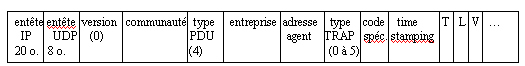
Figure 4: IP datagram for a SNMP TRAP
Two remarks are to be made:
SMI Structure:
The SMI structure describes the rules for describing an information, a parameter. It allows to identify in a single way an object of the MIB database managed by a SNMP agent. Each object thus has a single identifier or OID (Object ID).SMI also defines the data representation (and its type) for each MIB object. An MIB object is declared and defined in the ASN.1 language (Abstract Syntax Notation 1).
SNMP onlys uses a small part of the ASN.1 language. For example, these ASN.1 types are used for SNMP:
MIB Structure:
The MIB is a database managed by a SNMP agent controlling the managed objects according to the SMI rules. It has a tree structure similar to this used in the DNS (Domain Name System) . One finds a nonamed root from which one absolutely defines an object by its OID (the tree node).
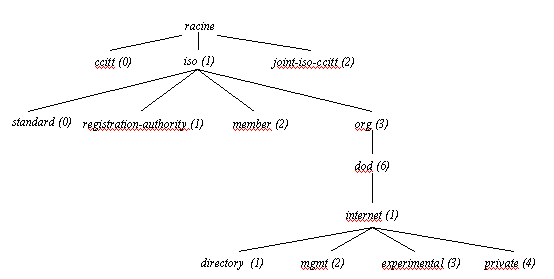
Figure 5: the SMI structure
If we make a zoom on the branch Internet, we have:
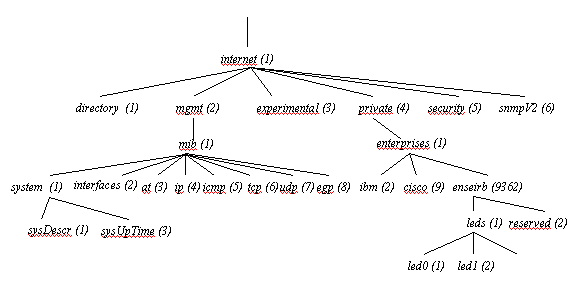
Figure 6: MIB zoom on the branch Internet
Each node has a readable string reference. Each object could be identified by a readable string or by its OID.
For example, the sysDescr object has like string reference iso.org.dod.internet.mgmt.mib.system.sysDescr.0 . Its OID according to the SMI rules is 1.3.6.1.2.1.1.1.0.
One can see that the interesting objects all have an OID starting by 1.3.6.1.2.1.
It should be noted that it's the OID which is transmitted in a SNMP request and not the string reference.
The MIB contains standard objects: it's the standard MIB. If a SNMP agent must manage its own objects, they belong the a private MIB. These objects are located in the branch iso.org.dod.internet.private.enterprises.enterprise_name. One "extends" the MIB of the SNMP agent. It is advisable for that to ask for an identifier to the IANA authority (Internet Assigned Numbers Authority). For example, the assigned number to the ENSEIRB School of Electrical Engineering and Computer Science is 9362.
The objet led0 has as string reference iso.org.dod.internet.private.enterprises.enseirb.leds.led0.0 . Its OID is 1.3.6.1.4.1.9362.1.1.0.
One can notice that the access to a simple MIB object (sheet of the tree) is done by adding 0 like suffix to the OID.
1.3. SNMP Versions
In 1993, new RFCs (RFC 1441 to 1452) were added to revise SNMPv1 (RFC 1155 to 1157) and to define SNMPv2c (classic). SNMPv2c was updated in 1996 (RFC 1901 to 1908) to give SNMPv2.
The principal differences between SNMPv1 and SNMPv2 are:
Unfortunately, SNMPv2 was not deployed (in experimentation). There exists also SNMPv3 (RFC 2571 to 2575) in gestation...
These hesitations and various versions scramble the
game. It will thus be retained that the only stable and official version is
SNMPv1 (with its lacks...).
2. NET-SNMP Implementation under Linux
2.1. Introduction
The SNMP implementation under Linux will be done by using
the standard in the free software: the NET-SNMP package.
The NET-SNMP project called in the past UCD-SNMP
was historically developed by the American university Carnegie Mellon University
(CMU) and then improved and maintained now by the American university
University of California Davis (UCD).
NET-SNMP is in fact a whole of tools and functionalities:
NET-SNMP is ported to various systems and in particular on:
NET-SNMP supports SNMPv1, SNMPv2 and SNMPv3 from the SNMP agent side and from the SNMP manager side by using on line commands.
2.2. NET-SNMP Installation
The NET-SNMP installation is classical under Linux:
Decompression:
# cd
# tar -xvzf net-snmp-5.0.2.tar.gz
# ln -s net-snmp-5.0.2 net-snmp
Configuration. One will choose to use SNMPv1 by default:
# cd ~/net-snmp
# ./configure
Compilation:
# make
Installation:
# make install
The NET-SNMP Linux commands are copied in the /usr/local/bin and /usr/local/sbin directories. It will be necessary to add them in the PATH variable of environment.
The MIB files used from the SNMP manager side by the Linux commands are in the /usr/local/share/snmp/mibs directory.
2.3. NET-SNMP Agent Configuration
The NET-SNMP agent is the executable snmpd under the /usr/local/sbin directory. It has a general configuration named snmpd.conf to be copied in the /usr/local/share/snmp directory. An example file is provided. It is necessary to modify it according to what one wants to do. It is the EXAMPLE.conf file under ~/net-snmp .
An on line help is also available (# man snmpd.conf).
The most significant fields are:
Declaration of a machine and a IP network having access to the SNMP agent, local and mynetwork. The community is tst:
# sec.name community source
com2sec local localhost tst
com2sec mynetwork 192.9.201.0/24 tst
Group declaration for accessing to the SNMP objects managed by the SNMP agent for local and mynetwork:
####
# Second, map the security names into group names:
# sec.model sec.name
group local MyRWGroup v1
group local MyRWGroup v2c
group MyROGroup v1 mynetwork
group MyROGroup v2c mynetwork
Read/write access to the MIB objects for a local SNMP request and read only access for a remote SNMP request:
####
# Finally, grant the 2 groups access to the 1 view with different
# Write permissions:
# context sec.model sec.level match read notif Write
access exact MyROGroup "" any noauth all none none
access exact MyRWGroup "" any noauth all
all none
SNMP TRAPs validation in direction to a SNMP manager running on the machine localhost with the community tst:
####
# Traps and v2 traps enabled and feels to localhost
#
# command host to manage community
trapsink localhost tst
trap2sink localhost tst
Declaration of the sysLocation object in the branch system:
syslocation ENSEIRB, Bordeaux, France
Declaration of the sysContact object in the branch system:
syscontact Kadionik <kadionik@enseirb.fr>
The snmpconf tool makes it possible to create the file snmpd.conf in an interactive and convivial way without knowing its structure.
Fast creation of the snmpd.conf file at the first use:
# snmpconf -g basic_setup
Interactive mode:
# snmpconf
After the snmpd.conf file creation, it must be copied in the /usr/local/share/snmp directory. The SNMP agent can be started:
# snmpd
One can start in another window a network sniffer like tcpdump to dump the exchanges between the SNMP agent and a SNMP manager:
# tcpdump -vv -i lo
2.4. NET-SNMP Agent Testing
The NET-SNMP agent testing is done by using a SNMP manager. The NET-SNMP package provides on line Linux commands for that under the /usr/local/bin directory in order to send SNMP requests.It is important to configure its Linux environment. To access to the MIB objects managed by the SNMP agent in the symbolic form and not in the decimal form (OID), it is necessary to read the whole MIB files under the /usr/local/share/snmp/mibs directory:
#
# PATH
#
PATH=$PATH:/usr/local/bin:/usr/local/sbin
#
# MIBS: forces to read all MIB files under/usr/local/share/snmp/mibs
#
MIBS=ALL
#
# exporting all variable
#
export PATH MIBS
The main snmpxxx Linux commands are:
It is then possible to test the SNMP agent with the snmpxxx Linux commands.
Correspondance between an OID and its symbolic form:
# snmptranslate 1.3.6.1.2.1.1.3.0
SNMPv2-MIB::sysUpTime.0
Representation in a graphical form of the branch system by analysis of the MIB files under the /usr/local/share/snmp/mibs directory:
# snmptranslate -Tp -IR system
+ -- system(1)
|
+ - - - R -- String sysDescr(1)
|Textual Convention: DisplayString
|Size: 0..255
. . .
SNMPv1 request for having the current value of the sysUpTime object managed by the SNMP agent executed on the machine localhost:
# snmpget -v 1 -C tst localhost system.sysUpTime.0
SNMPv2-MIB::sysUpTime.0 = Timeticks: (12908)
0:02:09.08
SNMPv2c request for having the current value of the sysUpTime object:
# snmpget -v 2c -C tst localhost system.sysUpTime.0
SNMPv2-MIB::sysUpTime.0 = Timeticks: (13966)
0:02:19.66
SNMPv1 request for having the current value of the sysLocation and sysContact objects (defined in the snmpd.conf file):
# snmpget -v 1 -C tst localhost system.sysLocation.0
SNMPv2-MIB::sysLocation.0 = STRING: ENSEIRB, Bordeaux, France
# snmpget -v 1 -C tst localhost system.sysContact.0
SNMPv2-MIB::sysContact.0 = STRING: Kadionik
<kadionik@enseirb.fr>
Walking the branch system of the MIB managed by the SNMP agent executed on the machine localhost:
# snmpwalk -v 1 -C tst localhost system
SNMPv2-MIB::sysDescr.0 = STRING: Linux poire1 2.4.18-3 #1 Thu Apr 18 07:31:07 EDT 2002 i586
SNMPv2-MIB::sysObjectID.0 = OID: Net-SNMP-MIB::netSnmpAgentOIDs
SNMPv2-MIB::sysUpTime.0 = Timeticks: (28119) 0:04:41.19
SNMPv2-MIB::sysContact.0 = STRING: Kadionik < kadionik@enseirb.fr >
SNMPv2-MIB::sysName.0 = STRING: poire1
SNMPv2-MIB::sysLocation.0 = STRING: ENSEIRB, Bordeaux, France
. . .
Affection of a new value to the sysLocation object with the SNMPv1 version:
# snmpset -v 1 -C tst localhost system.sysLocation.0 s "coucou"
Error in packet.
Reason: (noSuchName) There is variable No such name in this MIB.
Failed object: SNMPv2-MIB::sysLocation.0
Affection of a new value to the sysLocation object with the SNMPv2c version:
# snmpset -v 2c -C tst localhost system.sysLocation.0 S "coucou"
Error in packet.
Reason: notWritable (that object does not support modification)
Failed object: SNMPv2-MIB::sysLocation.0
By comparing the result of the 2 last Linux commands, one can see that SNMPv1 does not return an error code, which corrects SNMPv2c. In this case, one tries to modify a read only MIB object.
The tcpdump trace generated by the execution of the following Linux command:
# snmpget -v 1 -C tst localhost sysUpTime.0
is:
# tcpdump -vv -i lo
tcpdump: listening on lo
15:17:54.733310 poire1.1092 > poire1.snmp: [ UDP sum ok ]|30|26|02|01{ SNMPv1|04|03C=tst|a0|ç{ GetRequest(28)|02|04R=691700679|02|01|02|01|30|0e|30|0c|06|08system.sysUpTime.0|05|00} } (DF) (ttl 64, id 0, len 68)
15:17:54.734564 poire1.snmp > poire1.1092:
[ UDP sum ok ]|30|29|02|01{ SNMPv1|04|03C=tst|a2|1f{ GetResponse(31)|02|04R=691700679|02|01|02|01|30|11|30|0f|06|08system.sysUpTime.0
=|43|03127125} } (DF) (ttl 64, id 0, len 71)
One can see that the community (here tst) which it is necessary to consider as a password in uncrypted with SNMPv1.
It should be noted that one can also generate SNMP TRAPs by using the snmptrap Linux command. The daemon snmptrapd (under the /usr/local/sbin directory) can be used as SNMP TRAP collector. It uses the configuration file snmptrapd.conf that one must copy under the /usr/local/share/snmp directory. This configuration file can be automaticaly generated by using the snmpconf tool like previously.
3. Hardware Module for SNMP Testing
A small hardware module connected to the parallel port of a PC is proposed in order to illustrate the possibilities of remote control by SNMP. The final goal is to control a remote electronic system (embedded system) by SNMP.
The general diagram of this module is given below.
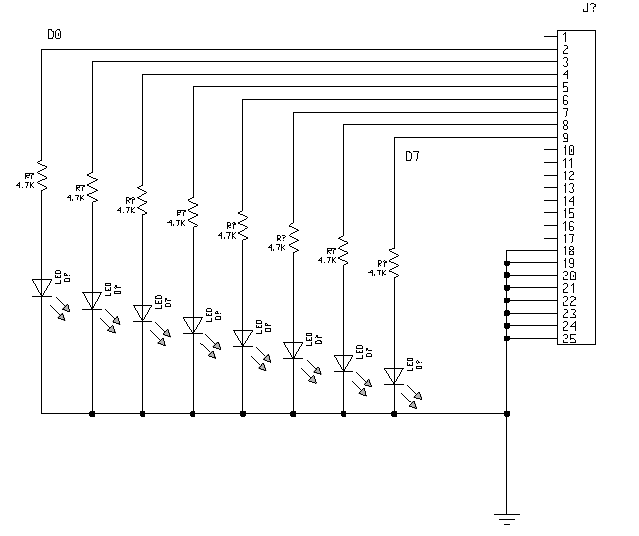
Eight leds are respectively connected to the data signals D0.. D7 of the PC parallel interface.
The film for the realization of the printed circuit
in simple face is given below. It's possible to recover the PostScript file
at the scale 1 at the WWW URL given at the end of this article.
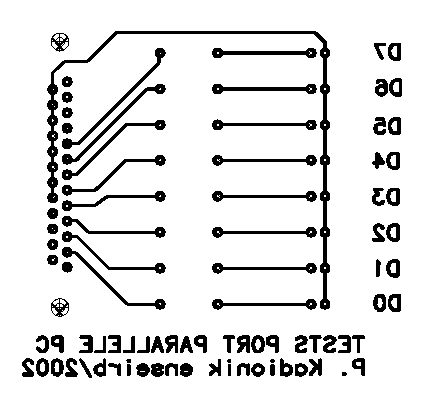
Figure 8: film of the hardware module
For the hardware specialists, the Gerber and drill files are available too.
One needs:
The layout diagram is given below.
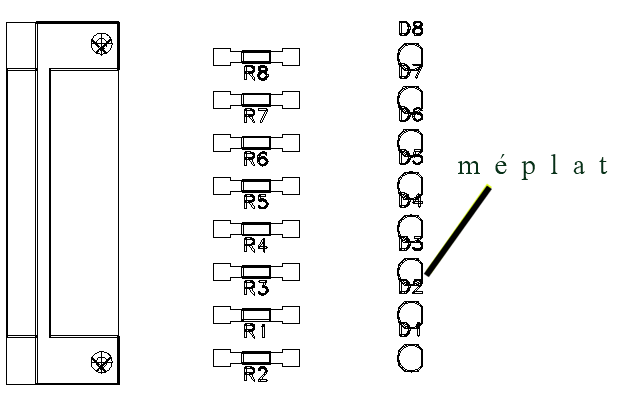
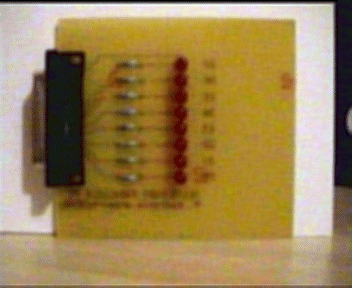
Figure 10: photo of the electronic module
There are no precautions particular to respect: just avoid the short-circuits during the realization of the printed circuit board.
Once the electronic module connected to the PC, it is possible to test it by using the provided test programs. The source files readleds.c and writeleds.c will be compiled to produce the executables readleds and writeled:.
# writeleds 0
Leds written = 0x00
# readleds
Leds read = 0x00
The following Linux command switchs on the 8 leds:
# writeleds FF
Leds written = 0xff
The following Linux command switchs on the even leds (D0...) and switchs off the odd leds (D1...):
# writeleds 55
Leds written = 0x55
The following Linux command switchs on the odd leds and switchs off the even leds:
# writeleds AA
Leds written = 0xaa
The Bourne shell script k2000.sh makes it possible to carry out a chenillard:
# k2000.sh
These 3 programs must be executed as a root in order to be able to drive the PC parallel port.
4. SNMP Control of an electronic System under Linux
The goal of this part is to explain how to extend the NET-SNMP agent for controlling the electronic module by SNMP. The traditional manner to control an electronic system remotely is to embed a Web server. Embedding SNMP is another more original way for doing the same thing but compatible with all network management software (HP Openview...).
4.1. Writing the MIB File in ASN.1
The first thing to be made is to create a ASCII file MIB-ENSEIRB.txt written in ASN.1 describing the new objects to be integrated in the private MIB of the NET-SNMP agent. One must create an MIB object for each led to control on the electronic module. This extension is always done in the branch private of the tree of the MIB. It should be noted that it is necessary for a company to have a single identifier (9362 for the ENSEIRB school) given by the IANA authority.
SNMP uses only a part of the ASN.1 language (X.208 ITU-T
recommendation) and one will be able to take as a starting point the files under
the /usr/local/share/snmp/mibs directory as
model.
ENSEIRB-MIB DEFINITIONS::= BEGIN
IMPORTS
enterprises FROM SNMPv2-SMI,
MODULE-IDENTITY FROM SNMPv2-SMI
MODULE-COMPLIANCE, OBJECT-GROUP FROM SNMPv2-CONF;
--
-- A brief description and update information about this mib.
--
enseirb MODULE-IDENTITY
LAST-UPDATED "0104010000Z" -- 01 Apr 2001, midnight
ORGANIZATION "ENSEIRB"
CONTACT-INFO "
Author: Patrice Kadionik
ENSEIRB, School of Electrical Engineering
postal: PO Box 99
33402 TALENCE CEDEX
FRANCE
email: kadionik@enseirb.fr
phone: +33-5-56-84-65-00
"
DESCRIPTION "MIB for remote control by SNMP
"
::= { enterprises 9362 }
leds OBJECT IDENTIFIER::= { enseirb 1 }
reserved OBJECT IDENTIFIER::= { enseirb 2 }
--
-- LED 0 connected to the PC parallel port
--
led0 OBJECT-TYPE
SYNTAX Integer32 (0..1)
MAX-ACCESS read-write
STATUS current
DESCRIPTION
"Led 0 connected to bit 0 of the PC parallel port."
DEFVAL { 0 }
::= { leds 1 }
. . .
--
-- LED 7 connected to the PC parallel port
--
led7 OBJECT-TYPE
SYNTAX Integer32 (0..1)
MAX-ACCESS read-write
STATUS current
DESCRIPTION
"Led 7 connected to bit 7 of the PC parallel port."
DEFVAL { 0 }
::= { leds 8 }
END
The ENSEIRB-MIB.txt file will be then recopied under the /usr/local/share/snmp/mibs directory in order to be able to use the snmpxxx Linux commands with the symbolic form.
One will be able to test the file created and to correct the possible detected syntax errors by using the Linux command:
# snmptranslate -Tp -IR enseirb
+--enseirb(9362)
|
+--leds(1)
| |
| +-- -RW- Integer32 led0(1)
| | Range: 0..1
| +-- -RW- Integer32 led1(2)
| | Range: 0..1
| +-- -RW- Integer32 led2(3)
| | Range: 0..1
| +-- -RW- Integer32 led3(4)
| | Range: 0..1
| +-- -RW- Integer32 led4(5)
| | Range: 0..1
| +-- -RW- Integer32 led5(6)
| | Range: 0..1
| +-- -RW- Integer32 led6(7)
| | Range: 0..1
| +-- -RW- Integer32 led7(8)
| Range: 0..1
|
+--reserved(2)
These are 8 objects in the branch enseirb.leds. Their type is a 32 bit integer accessible in read/write mode in the range 0..1.
One chooses as convention the 0 value for switching off a led and 1 for switching on it.
4.2. NET-SNMP Agent Extension
It is now possible
to integrate in the NET-SNMP agent the branch enseirb
under the branch iso.org.dod.internet.private.enterprises
(see figure 6) and the actions associated with switching on/off the
8 leds of the electronic module.
The tool mib2c written in the Perl language needs specific
Perl modules to install before use:
# cd ~/net-snmp
# cd perl
# cd default_store
# perl Makefile.PL
# make
# make install
# cd ..
# cd SNMP
# perl Makefile.PL
# make
# make install
The installation is now complete. One can now use the tool mib2c. mib2c makes it possible to transform a MIB file written in ASN.1 into C files which will be then compiled with the NET-SNMP agent in order to extend it. One can notice that:
# cd ~/net-snmp
# cd agent/mibgroup
# mib2c -c ../../local/mib2c.scalar.conf enseirb
writing to enseirb.h
writing to enseirb.c
running indent on enseirb.h
running indent on enseirb.c
There is generation of C source files C enseirb.c and enseirb.h which one will modify to control the electronic module. mib2c takes as parameter a SNMP object in the symbolic form , enseirb in our case.
It is now possible to modify the file enseirb.c to order to integrate the C code for driving the electronic module. This file contains the integration of the ENSEIRB MIB in the MIB of the NET-SNMP agent. One will note the presence of functions handlers for each object added in the MIB for SNMP requests GET and SET. These functions are called here do_led0() ..., do_led7() .
A finite state machine (FSM) is use to treat the SNMP requests. One will note the following characteristic states:
The last stage is recompiling the NET-SNMP agent:
# cd ~/net-snmp
# ./configure --with-mib-modules=enseirb
# make
# make install
4.3. NET-SNMP Agent Extension Testing
It is necessary to restart the NET-SNMP agent.
The following switches allow to debug the NET-SNMP agent extension enseirb introduced by the macro DEBUGMSGTL():
# snmpd -L -Denseirb
The following command dumps to screen each incoming and outcoming SNMP requests like tcpdump:
# snmpd -Ld -Denseirb
In order to drive the leds of the electronic module by SNMP, one uses the snmpxxx Linux commands:
Current value of the 8 leds:
# snmpwalk -c tst -v 1 localhost enseirb
ENSEIRB-MIB::led0.0 = INTEGER: 0
ENSEIRB-MIB::led1.0 = INTEGER: 0
ENSEIRB-MIB::led2.0 = INTEGER: 0
ENSEIRB-MIB::led3.0 = INTEGER: 0
ENSEIRB-MIB::led4.0 = INTEGER: 0
ENSEIRB-MIB::led5.0 = INTEGER: 0
ENSEIRB-MIB::led6.0 = INTEGER: 0
ENSEIRB-MIB::led7.0 = INTEGER: 0
Current value of the led 0:
# snmpget -c tst -v 1 localhost led0.0
ENSEIRB-MIB::led0.0 = INTEGER: 0
Switching on the led 0:
# snmpset -c tst -v 1 localhost led0.0 i 1
ENSEIRB-MIB::led0.0 = INTEGER: 1
Bad parameter. Must be between 0 and 1:
# snmpset -c tst -v 1 localhost led0.0 i 2
led0.0: Value out of range (2)
Current value of the led 0:
# snmpget -c tst -v 1 localhost led0.0
ENSEIRB-MIB::led0.0 = INTEGER: 1
Switching on the led 7:
# snmpset -c tst -v 1 localhost led7.0 i 1
ENSEIRB-MIB::led7.0 = INTEGER: 1
Final current state of the 8 leds:
# snmpwalk -c tst -v 1 localhost enseirb
ENSEIRB-MIB::led0.0 = INTEGER: 1
ENSEIRB-MIB::led1.0 = INTEGER: 0
ENSEIRB-MIB::led2.0 = INTEGER: 0
ENSEIRB-MIB::led3.0 = INTEGER: 0
ENSEIRB-MIB::led4.0 = INTEGER: 0
ENSEIRB-MIB::led5.0 = INTEGER: 0
ENSEIRB-MIB::led6.0 = INTEGER: 0
ENSEIRB-MIB::led7.0 = INTEGER: 1
The bourne shell script k2000snmp.sh makes it possible to have a luxurious chenillard with SNMP:
# k2000snmp.sh
4.4. SNMP TRAP Generation
It is also possible
to send SNMP TRAPs from the NET-SNMP agent. In the file enseirb.c, when the led0 goes from on to off, the
NET-SNMP agent sends a TRAP (specific number 100) to SNMP managers defined in
its configuration file snmpd.conf. One uses
for that the function send_easy_trap() of the
NET-SNMP API.
The tcpdump trace generated in this case is:
14:59:01.316389 poire1.1090 > poire1.snmptrap:
[udp sum ok] |30|27|02|01{ SNMPv1 |04|03C=tst |a4|1d{ Trap(29) |06|09E:8072.4.0
|40|040.0.0.0|02|01 enterpriseSpecific|02|01[specific-trap(100)!=0] |43|0213784|30|00}
} (DF) (ttl 64, id 0, len 69)
The Linux command snmptrapd (daemon) makes it possible to collect all received SNMP TRAPs. The following Linux command dumps them to screen:
# snmptrapd -P
2002-07-04 14:56:29 NET-SNMP version 5.0.1 Started.
2002-07-04 14:56:56 poire1 [udp:127.0.0.1:1089]:
RFC1213-MIB::sysUpTime.0 = Timeticks: (1292) 0:00:12.92 SNMPv2-MIB::snmpTrapOID.0 = OID: NET-SNMP-MIB::netSnmpNotifications.0.100
2002-07-04 14:56:56 0.0.0.0(via udp:127.0.0.1:1090) TRAP, SNMP v1, community tst
NET-SNMP-MIB::netSnmpNotifications Enterprise Specific Trap (100) Uptime: 0:00:12.92
5. Controlling by SNMP an embedded System under µCLinux
We present now how to extend the NET-SNMP agent ported to µClinux. We use here an evaluation board from Motorola (ColdFire 5407C3 board).
The NET-SNMP agent extension under µClinux is similar as what it has been done under Linux.
One want to control by SNMP the leds of the Motorola evaluation board.
For that, one must develop the MIB file for NET-SNMP agent extension. One uses the same file MIB-ENSEIRB.txt because the evaluation board has 8 leds too.
One installs now under Linux NET-SNMP version 4.2.1 because it's the NET-SNMP version ported to µClinux (version 20020927) and the skeleton files generated with mib2c are not compatible with the NET-SNMP version 5.
One uses then the tool mib2c under Linux to create the skeleton files enseirb.c and enseirb.h which will be modified in consequence to control the 8 leds of the Motorola board.
The files thus created are recopied in the µClinux distribution under the ~/µClinux/user/ucdsnmp/agent/mibgroup directory.
The only difficulty is then to modify the Makefile files and header files under ~/µClinux/user/ucdsnmp to take into account the compilation of the files enseirb.c and enseirb.h.
The µClinux kernel must be recompiled by including the package ucdsnmp. The image file is then downloaded into the evaluation board and the NET-SNMP agent is tested then as under Linux.
One thus sees one of the major interests of the NET-SNMP package: it is easily portable to be integrated into an embedded Linux and thus to be embedded into an electronic system for a remote control by SNMP...
6. SNMP and Security
One cannot say that SNMP is a secure protocol in particular with the SNMPv1 version. The community has to be considered as a password which is transmitted uncrypted on the network (see the previous tcpdump traces).
SNMPv1 is also unsecure. Unfortunately, it is the only SNMP protocol allowed and supported by all the equipments.
If one does not need to use a SNMP agent on a equipment or on an embedded system, one will not activate this service by default. In this case, it will be necessary to check its configuration file (snmpd.conf for NET-SNMP) and to adopt the policy of the "whole prohibited except" and not "whole allowed except" in order not to leave holes in security. It will also be necessary to change the default community names which are generally public for the read access and private for the write access to the MIB objects. If it is not the case, a cracker could very easily remotely shutdown by SNMP a equipment, and even worse: it was seen previously that it is possible to control electronic systems by SNMP: switching off a led or shutting down an equipment is the same thing...
7. SNMP Managers
These are SNMP managers having a convivial GUI for managing a network by SNMP. There is the great classic HP Openview manager in the commercial field. A free SNMP manager is Loriot developed by Ludovic Lecointe. This SNMP manager runs under Windows and is really very complete. One can cite its following functionalities:
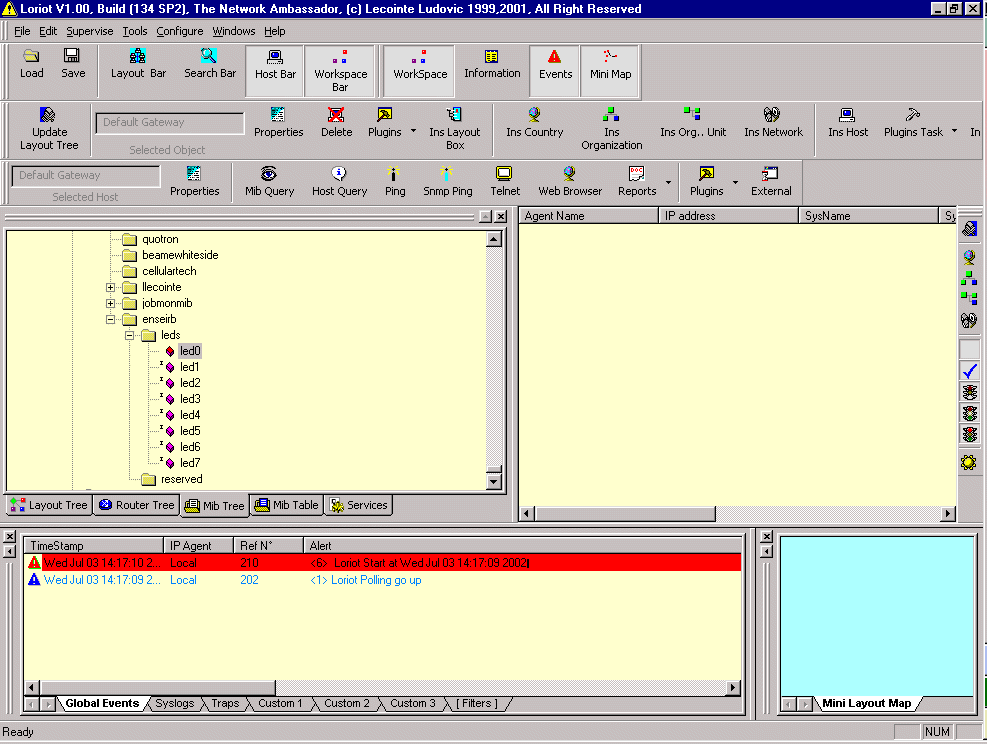
Figure 11: Loriot SNMP manager
It is provided with the NET-SNMP package a MIB browser
tkmib developped in the Tk language which makes it possible to visualize the
MIB files of the /usr/local/share/snmp/mibs
directory. One can also send SNMP requests.
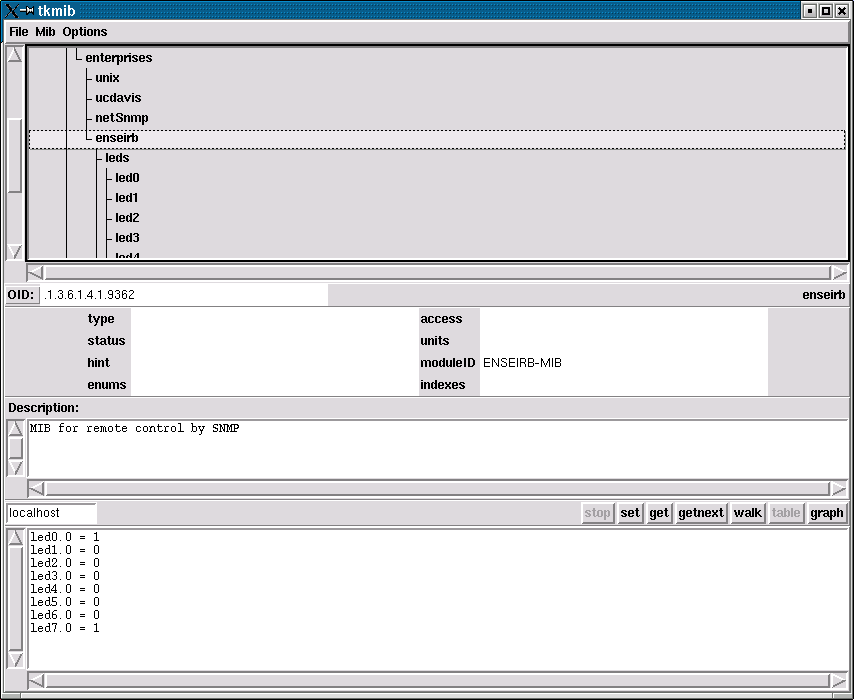
Figure 12: tkmib MIB browser
There is a more complete solution under Linux called Scotty. It is in fact a Tcl extension for network management.
Tkined is a Tk GUI using Scotty making it possible to manage a network. It belongs to the Scotty package.
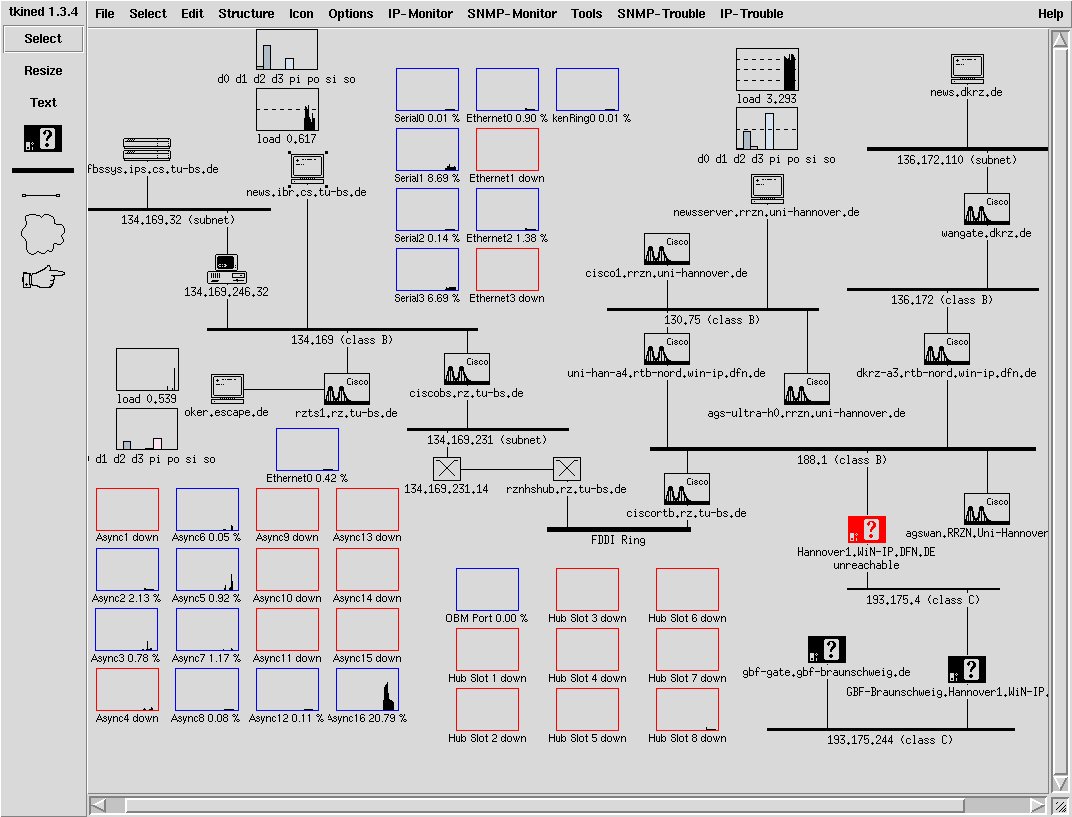
Figure 13: Tkined SNMP manager
8. Conclusion
We have seen through this article the importance of the network management which is one of the tasks which generally falls to the system administrator. For a telecom operator, the task is very difficult because it is essential for him to keep its network in operating state and to react as fast as possible in the event of breakdown.
The SNMP protocol was developed to facilitate the network management. We have seen that with simple SNMP requests (GET, SET...) and SNMP TRAPs, it is possible to manage a network. We have also presented the free software package for that: NET-SNMP.
In the case of the embedded systems, we have presented how to extend the NET-SNMP agent in order to control remotely by SNMP an electronic system under the Linux or µClinux OSs. It is a method a little less traditional than using an embedded Web server. NET-SNMP makes it possible to integrate an embedded system into a network and to manage it with SNMP managers like HP Openview.
SNMPv1 is the version of the SNMP protocol supported
and adopted by all. It has large holes of security. Consequently, you will never
activate a SNMP agent for fun or leasure or you'll see one day your machine
shutting down suddenly without explanation!
The whole of the schematics of the electronic module and programs used in this article are available to the following WWW address: http://www.enseirb.fr/~kadionik/embedded/snmp/annexe.html
References
Literature:
The RFC available at http://www.rfc-editor.org/
RFC1156. Management Information Base Network Management of TCP/IP based Internets
RFC1157. SNMP: Simple Network Management Protocol
RFC1158. Management Information Base Network Management of TCP/IP based Internets: MIB-II
RFC1212. Concise MIB definitions.
RFC1213. MIB-II: Management Information Base for network management of TCP/IP based Internets
RFC1215. Convention for defining traps for uses with SNMP
RFC1270. SNMP communications services
RFC1303. With Convention for Describing SNMP-based Agents
RFC1351. SNMP Administrative Model
RFC1352. SNMP Security Protocols
RFC1353. Definitions of Managed Objects for Administration of SNMP Left
RFC1442. Structure of Management Information for SNMP version 2
RFC1443. Textual Conventions for SNMP version 2
RFC1445. Administrative Model for SNMP version 2
RFC1446. Security Protocols for SNMP version 2
RFC1447. Party MIB for SNMP version 2
RFC1448. Protocol Operations for SNMP version 2
RFC1449. Transport Mappings for SNMP version 2
RFC1450. Management Information Base for SNMP version
2
Software: